Access control: Managing users
User management page
This page is accessed via Admin > Users & Groups in the main menu. The page lists all users, both local and external.
User management operations available to Administrators are the following:
- Create new user accounts.
- Edit existing user accounts.
- While editing a user account, change a user's password.
- Delete existing user accounts.
- While deleting an existing user, transfer their shared assets to another user.
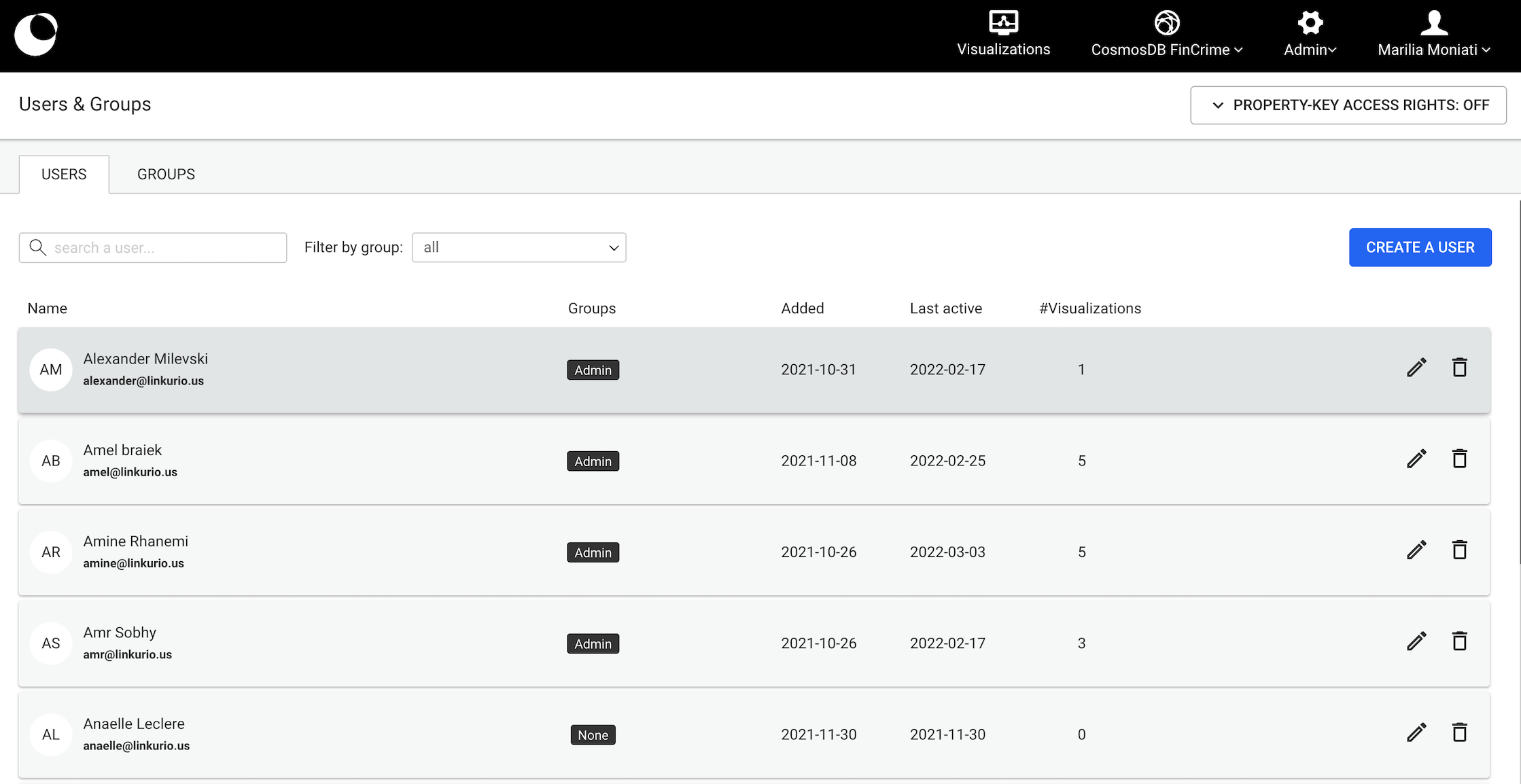
Deleting a user and transferring their shared assets
When deleting a user who has shared assets, admins are able to transfer these to an eligible user. Shared assets are visualisations, widgets, queries, custom actions or alerts which have been shared with at least one other user. Eligible users, are all admins and users who share the same access right group(s) as the to-be-deleted user.
Below, useful information on the characteristics of each asset and their sharing options can be found:
Visualisations
A visualisation can be shared to all the users who have access to the datasource. The owner of a visualisation is able to set the access rights for each user who has access to the visualisation. A visualisation is considered a shared asset when it's shared with at least one user.
Widgets: If a visualisation has a widget, even if the visualisation is not shared, when the widget is transferred to a user, so is the visualisation.
Visualisation folders cannot be shared explicitly with users but they are transferred when they include a shared visualisation which is handed over. ( note this does not appear in the number of shared assets which is shown in the deletion modal )
Alerts, Custom Actions and Queries
- These are shared according to group access rights.
Assigning users to groups
In order to be able to access Linkurious Enterprise, users need to be assigned to at least 1 user group.
A user can be assigned to:
- At most 1 built-in group
- Multiple custom groups
Group assignment can be done either while creating or editing a user account.
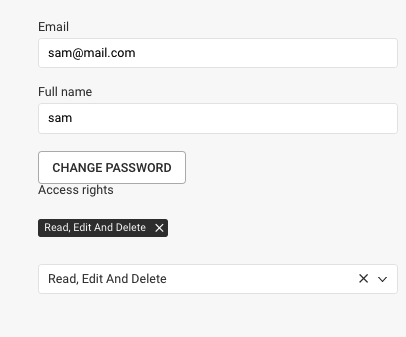
Assigning users to groups can be automated if you are using external authentication, using group mapping.